Step-based approach to prepare for a cyberattack
Security testing can be used to simulate different types of hacker skills in order to prepare for a real cyberattack. It allows organisations to assess their maturity by identifying vulnerabilities regarding people, processes and technology. It also allows them to increase cyber resilience by training the organisation to respond effectively.
Published: 08 July 2025

Using the step-based approach (Figure 1) from De Nederlandsche Bank (DNB), this article describes how to build a mature security organisation and learn from each security test. It also explains how various security tests with increasing organisational impact can enhance the cyber resilience of the entire organisation. Rob Wassink developed the step-based approach based on his experience as a cyber security specialist and Test Manager at DNB’s department of Cyber Resilience and Crisis Management.
Institutions can use the step-based approach to create an information security roadmap to build a mature security organisation and increase cyber resilience through security testing.
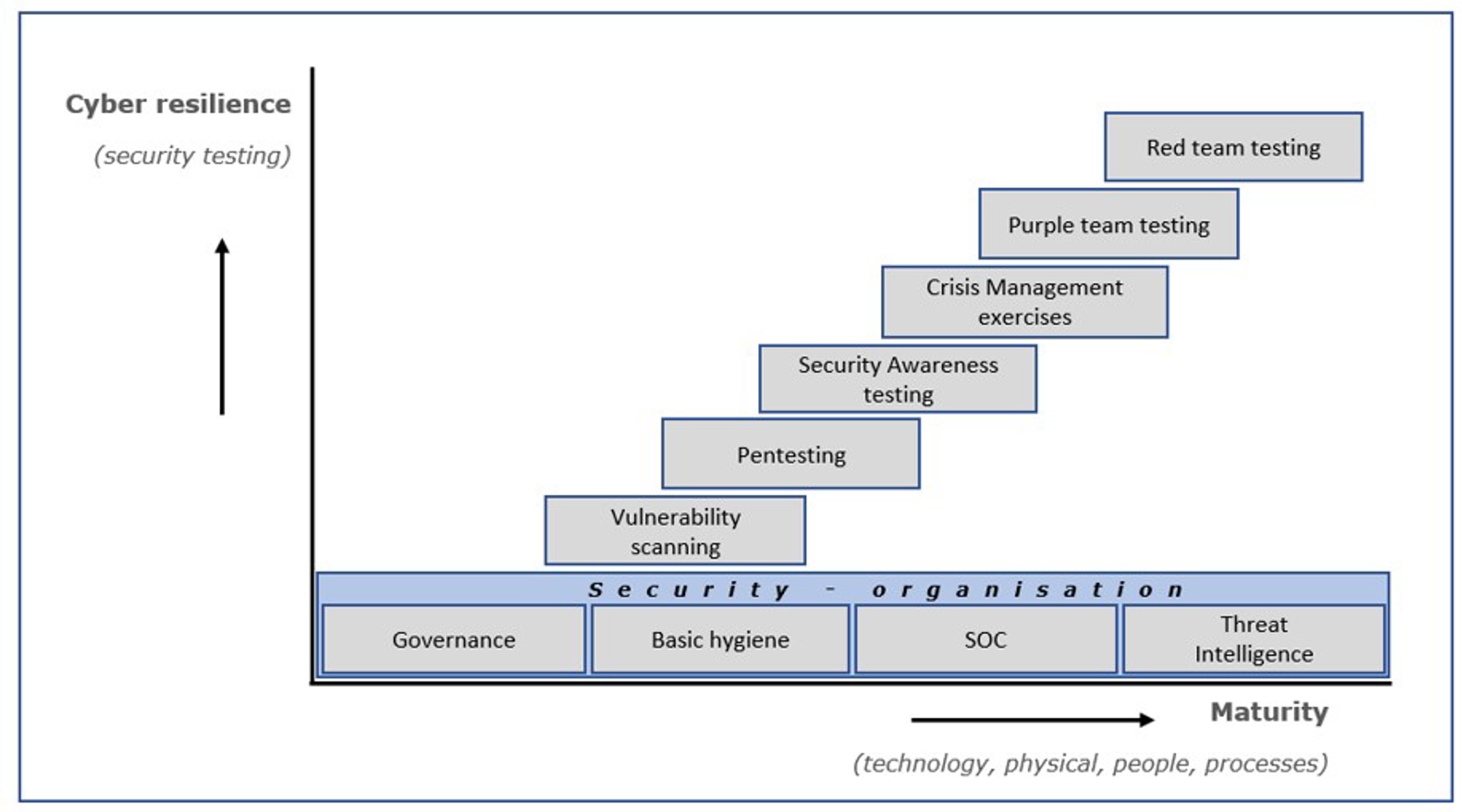
© DNB
Figure 1: Step-based approach to build a mature security organisation and increase cyber resilience Source: DNB Cyber Resilience & Crisis Management
Building a mature security organisation and increasing cyber resilience.
The horizontal axis in Figure 1 shows the four aspects of information security that should be implemented to build a mature security organisation.
The vertical axis shows the security tests (with increasing organisational impact) for increasing the organisation’s cyber resilience.
The sequence of security testing is not set in stone. It is important that tests are repeated regularly, and that test results are evaluated and acted upon to continuously improve the security organisation.
Set up an information security testing roadmap to prepare for a real cyberattack
The CISO defines a target end state for the organisation’s maturity of information security and cyber resilience by knowing the business objectives and being aware of relevant cyber threats. This entails people, processes, technology and physical aspects. A security testing strategy can be defined based on the target end state, taking into account the CIA rating of critical functions and their supporting information systems. This can help the organisation to comply with Digital Operational Resilience Act (DORA).
After management board approval, the CISO sets up an organisational structure for managing information security risks. This could be done by installing an information security steering group representing first line management, chaired by the CISO. The steering group then conducts gap analyses on each step as shown in Figure 1. Changes and actions to be performed over time to close identified gaps and reach the target end state can be summarised in an information security testing roadmap.
The plan-do-check-act (PDCA) cycle must be followed to guarantee and continuously improve the quality of planned actions and implemented security measures. The CISO is responsible for coordinating and checking implemented measures while reporting on status and progress to the management board. This step-based approach can help organisations improve their information security and prepare for a real cyberattack.
Description of each step
The text below explains each step shown in Figure 1. While not exhaustive, it briefly explains the topics that can be considered when implementing each step.
Horizontal axis: building a mature security organisation
A mature security organisation has implemented four aspects of information security. Each aspect is described below:
Governance
A CISO or a similar role is usually responsible for information security with a direct reporting line to the management board, which is ultimately responsible for information security. The first line of management in each department must comply with laws, regulations and documented information security policies.
The first line is responsible for implementing information security measures on organisational aspects related to their own scope. This could be people (all employees including management), processes (including business processes), technology (IT infrastructure and business applications), physical security (office building, datacentre) and outsourced services.
It is important that, together with the CISO, these first-line managers from all associated departments (such as business management, Human Resources, IT, Facility Management, and both Contract and Service delivery management) are aware of their role and responsibility regarding information security. The CISO can set up and chair an information security steering committee and meet with these managers regularly. These meetings serve to advise on, coordinate and check implemented measures, while the CISO reports on status and progress to the management board.
Basic hygiene
Organisations must identify their critical business functions (crown jewels) and underlying information systems and services, including all endpoints. Together, these form the attack surface of the organisation for hacker groups or so-called threat actors. The attack surface combined with the context of the organisation, its role in the supply chain and outsourced services can help to identify information security and third-party risks.
Risk management is the process of identifying, assessing and controlling these risks. It is the core of basic hygiene and provides insight into which assets need to be protected and which baseline measures need to be taken. ISO27005 is the international standard that describes how to identify, evaluate and manage information security risks. It can serve as a guideline for organisations wishing to increase their maturity. User access control, back-up and restore procedures and offline back-up are important measures. ISO27002 is a supplementary standard and provides a baseline of security measures that organisations can select and implement in a risk-based manner.
Financial institutions in the Netherlands must comply with the DORA regulations. In other sectors, organisations strive for ISO27001 certification, or a derivative such as NEN7510 for the Dutch healthcare sector, or BIO for the Dutch government. The goal of each standard is to be in control of information security.
SOC
The Security Operations Center (SOC) monitors, detects and manages security events and incidents. This is primarily the responsibility of dedicated SOC analysts. They monitor proactively, classify security events and respond to security incidents. They also initiate recovery procedures when the confidentiality integrity or availability of information systems has been compromised. The SOC can be internal or (partly) outsourced to a security provider.
The SOC uses a Security Information & Event Monitoring (SIEM) solution for monitoring and detecting events and security incidents. Therefore, it continuously collects and analyses large volumes of logfiles from the organisation’s critical systems. Use cases (alarm bells) can be defined manually to detect suspicious behaviour in these logfiles. Implementing a SIEM solution requires considerable coordination and effort. Security teams might be overwhelmed by the number of alerts (and false positives), causing the SOC to miss critical alerts.
To enable the SOC analysts to do their job more efficiently, Endpoint Detection and Response (EDR) and Network Detection & Response (NDR) can be implemented as well.
The EDR solution detects Indicators of Compromise (IoCs) on endpoints in the attack surface automatically by making use of worldwide shared operational threat intelligence. It can also detect abnormal and suspicious user behaviour on endpoints and respond automatically. While the EDR solution monitors each endpoint, the NDR solution can monitor and detect suspicious network activities and respond automatically.
Security orchestration, automation and response (SOAR) technology can help to coordinate, execute and automate tasks between various people and implemented security tools, all within a single platform.
Threat intelligence
Threat intelligence can provide the organisation with relevant threat information. It can be purchased from an external security provider, which provides regular updates. This allows organisations to anticipate new or escalating cyber threats with appropriate measures in a timely manner. While operational threat intelligence provides direct input for the SOC’s automated incident detection solutions, tactical threat intelligence can be used to investigate whether the organisation’s SOC is resistant to attack techniques, tactics and procedures (TTPs) from relevant international threat actors.
Vertical axis: increase cyber resilience through security testing
While the four aspects of a mature security organisation are being implemented and maturity demonstrably increases, security tests can be conducted that transition from technical tests to security tests with increasing organisational impact.
Vulnerability scanning
Vulnerability scanning is a basic technical security test and is part of vulnerability management. it is an automated and proactive process conducted by a scanning tool. It detects common vulnerabilities and exposures (CVEs) on endpoints, information systems and networks. Scanning tools can be purchased for this purpose and may run daily. By identifying and addressing potential security weaknesses, organisations can protect the attack surface against potential cyberattacks.
Pentesting
Pentesting stands for penetration testing. This test is used not only to search for technical vulnerabilities and to detect whether a combination of vulnerabilities in an information system or business process can be used to compromise information. It also focuses on vulnerability in people, processes and technology. Human creativity is used and the scope of a pentest is limited to components that form part of the attack surface. This can be a web application or another information system, sometimes extended to the physical room where the equipment is located and the people working with it.
The product owners who manage these information systems are responsible for pentesting their own systems and managing the results. Pentesting is often part of the process of developing and testing new systems, and is sometimes a prerequisite before taking a system into production.
Security awareness testing
Security awareness is important for all employees, including management. As most teams work with sensitive information, they can all play a part in protecting it. To this end, they must be aware of their role and responsibility in preventing attacks.
A security awareness programme focusses on changing people’s behaviour relating to information security. There are several ways to boost employee awareness, such as: awareness training (part of the onboarding process), online campaigns, and social engineering testing and phishing simulations. It is important that the CISO involves departments like HR and Communication in the security awareness programme.
Crisis management exercises
During tabletop exercises and more realistic crisis simulations, the organisation's crisis management team (CMT) practices scenarios in which a security incident escalates into a (cyber) crisis. A documented and up-to-date crisis management plan and well trained CMT are prerequisites for any organisation’s business continuity. Regularly challenging the CMT by practicing relevant crisis scenarios will boost the organisation’s resilience.
Purple team testing
For purple team testing, the organisation hires ethical hackers (a red team) to join the blue team (people from the SOC) for short technical sessions. Red + blue = purple, hence this name. In these technical sessions, the red and blue teams work together to investigate whether configured technical measures function effectively, and whether the blue team is able to detect and respond to the latest attack techniques (TTPs) used by relevant threat actors. Purple team sessions can be used to prepare the SOC for red team testing or for a real cyberattack.
Red team testing
Red team testing is the ultimate way to assess an organisation’s cyber resilience. For this type of testing, the organisation again hires ethical hackers (a red team) who play out at least one attack scenario, preferably based on relevant threat intelligence. All critical functions are in scope. The attack surface for the red team comprises the underlying production systems and services, including the organisation’s people, process and technology.
The blue team is not informed about the red team test, which makes the test even more realistic. Outsourced systems and services are sometimes out of scope in cases where suppliers (third parties) are not willing or able to take part in the red team test for legal reasons.
Red team testing is almost always followed by purple team testing to give the blue team insight into the scenarios played out and enable them to learn from retrospective analysis. The red team test scenario and findings during the test can also be used to define a realistic crisis management scenario.
To read more about different types of red team test frameworks, please see DNB oversees cyber resilience tests | De Nederlandsche Bank
Discover related articles
DNB uses cookies
We use cookies to optimise the user-friendliness of our website.
Read more about the cookies we use and the data they collect in our cookie notice.